Agent Sudo

Task 1 - Deploy the machine
Task 2 - Reconnaissance
Task 3 - Enumerate
3.1 - How many open ports?
command
result
3.2 - How you redirect yourself to a secret page?

3.3 - What is the agent name?


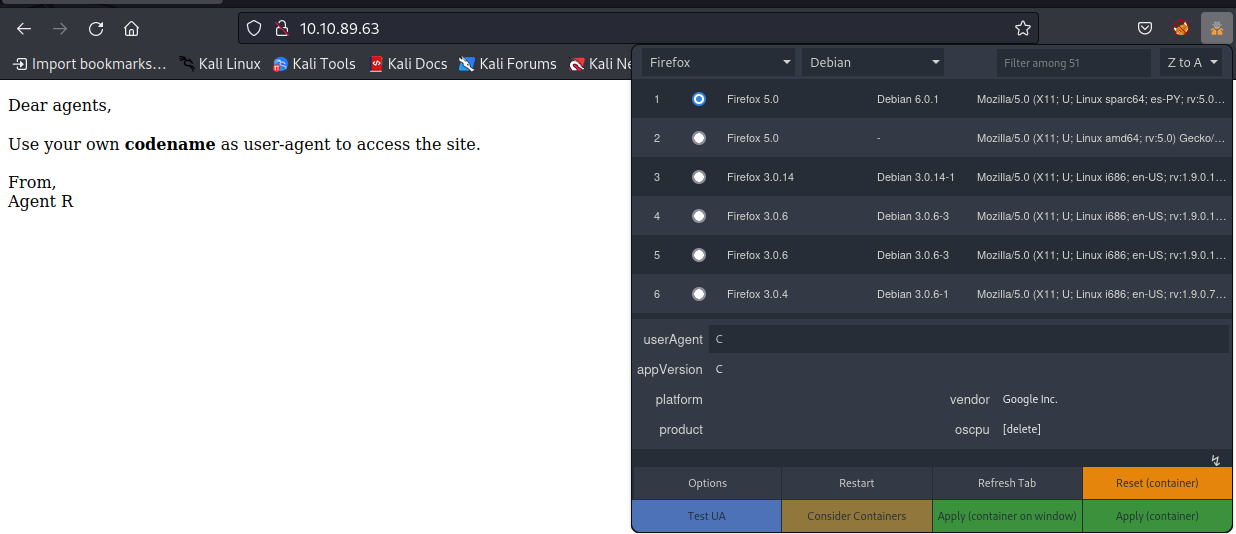
Task 4 - Hash cracking and brute-force
4.1 - FTP password
4.2 - Zip file password
4.3 - Steg password
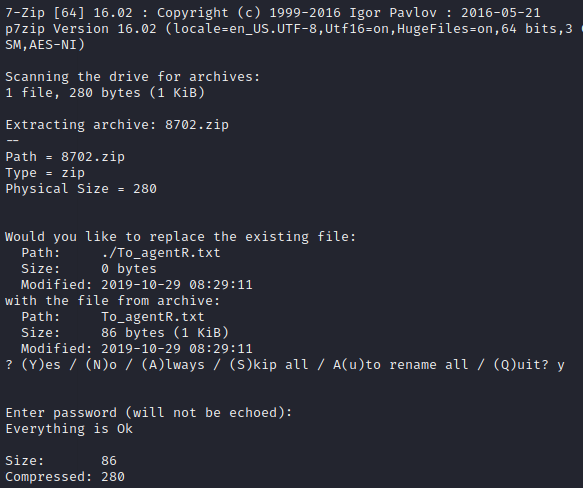
4.4 - Who is the other agent (in full name)?
4.5 - SSH password
Task 5 - Capture the user flag
5.1 - What is the user flag?
5.2 - What is the incident of the photo called?

Task 6 - Privilege escalation
6.1 - CVE number for the escalation



