Ignite

🔗 Ignite
Task 1 - Deploy the machine
🎯 Target IP: 10.10.166.221
Create a directory for machine on the Desktop and a directory containing the scans with nmap.
Task 2 - Reconnaissance
I prefer to start recon by pinging the target, this allows us to check connectivity and get OS info.
Sending these three ICMP packets, we see that the Time To Live (TTL) is ~64 secs. this indicates that the target is a *nix system (probably Linux), while Windows systems usually have a TTL of 128 secs.
2.1 - Find open ports on the machine
sudo
run as root
sC
run default scripts
sV
enumerate versions
A
aggressive mode
T4
run a bit faster
oN
output to file with nmap formatting
It looks like there are only one open port on the machine: HTTP.
Task 3 - What is the user flag?

We can search exploit with searchsploit:
Very good, there're many exploits for this CMS.
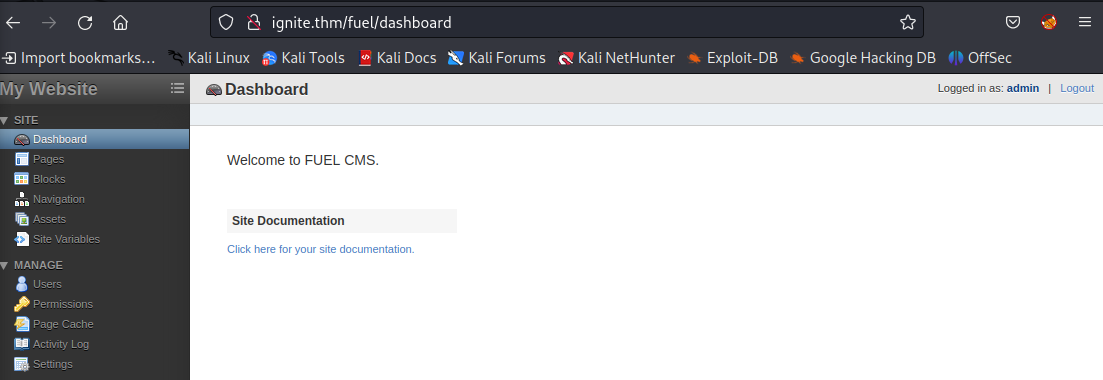
Exploring page we found a good info:

To access the FUEL admin, go to: http://ignite.thm/fuel User name: admin Password: admin (you can and should change this password and admin user information after logging in).

Now, we can try to exploit using a RCE exploit, first we download script from searchsploit db:
After this, we can launch exploit:
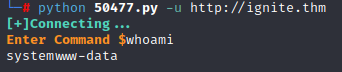
We need to do a reverse shell, we start to:
Retrieve our ip address:
and create a shell file with nano:
Insert this line for a bash reverse shell:
Setup a Python web server and a nc listener on 2 different tabs:
1st tab:
2nd tab:
Now, we can return in the exploited Fuel CMS tab, and do this commands:
Reverse shell received in the nc terminal: