2.3 Web Server Fingerprinting
Web Server Fingerprinting
A web server fingerprint is essentially a unique identifier or signature of a web server's software, configuration, and sometimes even its hardware characteristics. It's like a digital footprint that can reveal details about the server's underlying technology stack, such as the operating system, web server software (e.g., Apache, Nginx), version numbers, installed modules, and other relevant information.
Web server fingerprints can be obtained through various means, including:
HTTP Headers: Web servers often include specific headers in their HTTP responses that can reveal information about the server software and its version. For example, the "Server" header typically discloses the name and version of the server software being used.
Error Pages: The format and content of error pages (e.g., 404 Not Found) can sometimes provide clues about the web server software and its version.
Response Behavior: Certain behaviors or responses from the server can also be indicative of the server type and version. For example, the way the server handles certain requests or supports specific features may help identify it.
Banner Grabbing: This involves directly connecting to the server and analyzing the banners or initial responses it provides, which often contain information about the server software and version.
We can use following methods and tool to do a Web Server Fingerprint:
Nmap
👁️NmapWe can use Nmap for first scanning on all ports with the flag: -p0-
sudo nmap -p0- sV <Target> -oG nmap/portAfter it, we can use searchsploit to discover potential exploit and search nmap script and eventually grep for detailed results
ls -al /usr/share/nmap/scripts/ | grep -e "apache"
And e.g. use http-enum to discover port 80
--open
only open ports
sC
run default scripts
sV
enumerate versions
-p0-
search all ports [0 - 65535]
--min-rate
minimun packet sent for second
vvv
more verbosity
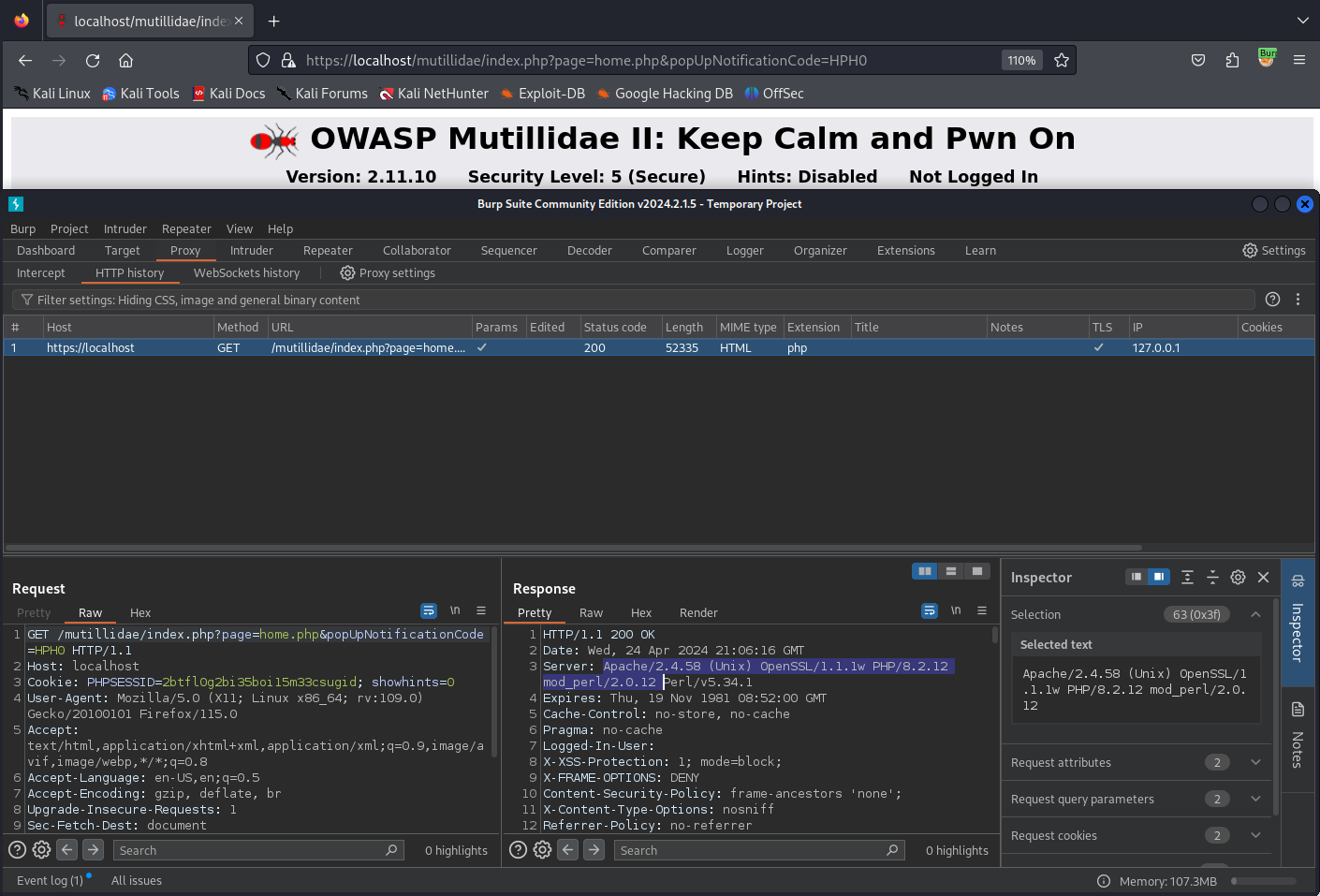
Burp Suite
Intercept request
Forward request
See WebServer value into response
Metasploit
We can use a metasploit module called http_version to retrieve info regarding webserver
use scannet/http/http_version
set rhosts <target>
run
Curl
Curl displays source code content (passive method)
curl http://<target>
Discovering specific folders with Brute Force tools
Or try to discover information regarding folders presents only in determinated webserver such as cgi-bin (Apache) and HttpClient (IIS). We can research folder using brute force tools like as: dirb, gobuster, wefuzz.
Web Server Scanning with Nikto
A great tool that help us for Web Server Scanning is Nikto, that permit us to:
Find SQL injection, XSS, and other common vulnerabilities
Identify installed software (via headers, favicons, and files)
Guess subdomains
Includes support for SSL (HTTPS) websites
Saves reports in plain text, XML, HTML or CSV
“Fish” for content on web servers
Report unusual headers
Check for server configuration items like multiple index files, HTTP server options, and so on
Has full HTTP proxy support
Guess credentials for authorization (including many default username/password combinations)
Is configured with a template engine to easily customize reports
Exports to Metasploit
Automated Web Recon With OWASP Amass
The OWASP Amass Project performs network mapping of attack surfaces and external asset discovery using open source information gathering and active reconnaissance techniques.
Information Gathering Techniques Used:
APIs
360PassiveDNS, Ahrefs, AnubisDB, BeVigil, BinaryEdge, BufferOver, BuiltWith, C99, Chaos, CIRCL, DNSDB, DNSRepo, Deepinfo, Detectify, FOFA, FullHunt, GitHub, GitLab, GrepApp, Greynoise, HackerTarget, Hunter, IntelX, LeakIX, Maltiverse, Mnemonic, Netlas, Pastebin, PassiveTotal, PentestTools, Pulsedive, Quake, SOCRadar, Searchcode, Shodan, Spamhaus, Sublist3rAPI, SubdomainCenter, ThreatBook, ThreatMiner, URLScan, VirusTotal, Yandex, ZETAlytics, ZoomEye
Certificates
Active pulls (optional), Censys, CertCentral, CertSpotter, Crtsh, Digitorus, FacebookCT
DNS
Brute forcing, Reverse DNS sweeping, NSEC zone walking, Zone transfers, FQDN alterations/permutations, FQDN Similarity-based Guessing
Routing
ASNLookup, BGPTools, BGPView, BigDataCloud, IPdata, IPinfo, RADb, Robtex, ShadowServer, TeamCymru
Scraping
AbuseIPDB, Ask, Baidu, Bing, CSP Header, DNSDumpster, DNSHistory, DNSSpy, DuckDuckGo, Gists, Google, HackerOne, HyperStat, PKey, RapidDNS, Riddler, Searx, SiteDossier, Yahoo
Web Archives
Arquivo, CommonCrawl, HAW, PublicWWW, UKWebArchive, Wayback
WHOIS
AlienVault, AskDNS, DNSlytics, ONYPHE, SecurityTrails, SpyOnWeb, WhoisXMLAPI
Perform automatic scan
Last updated