5.2.2 SUID Exploitation
SUID Exploitation
What is SUID?
SUID, which stands for Set User ID, is a special permission in Linux and Unix-like operating systems. When an executable file has the SUID permission set, it allows the user to execute the file with the privileges of the file's owner rather than the privileges of the user who is running the program. This is particularly useful for certain system programs that need elevated privileges to perform specific tasks.
The SUID permission is represented by the letter "s" in the user permission field of the file's permission bits. When the SUID bit is set, you will see an "s" instead of an "x" in the user permission field. For example:
If the SUID bit is set:
-rwsr-xr-xIf the SUID bit is not set:
-rwxr-xr-x
Common examples of programs that use the SUID permission include passwd and sudo. These programs need elevated privileges to perform tasks like changing the user password or running commands with superuser privileges.
It's important to note that the SUID mechanism should be used with caution, as it can introduce security risks. If a poorly designed program has the SUID bit set and contains vulnerabilities, it may be exploited to gain unauthorized access or perform malicious actions with elevated privileges. Therefore, system administrators should carefully review and audit programs with the SUID bit set to ensure they are secure and necessary for system functionality.
r=read, w=write, x=execute
rwx rwx rwx
user group others
421 421 421
4+2+1=7 4+2+1=7 4+2+1=7
chmod 777 #Maximum privilegesWhat is a SUID Exploitation?
SUID exploitation is a serious security concern and is often associated with unauthorized activities and hacking. System administrators should follow best practices in securing their systems, including proper configuration, regular updates, and auditing of permissions to minimize the risk of SUID-related vulnerabilities.
Here's a basic overview of SUID exploitation:
Understanding SUID:
SUID is a special permission that can be set on an executable file. When a user runs a program with the SUID bit set, the program runs with the privileges of the file owner rather than the user who is executing the program.
Exploitation Scenario:
An attacker looks for a vulnerable program with the SUID bit set. This could be a system utility or custom program that has a security flaw.
Identifying Vulnerabilities:
The attacker identifies vulnerabilities in the program that can be exploited to execute arbitrary code or commands. These vulnerabilities could include buffer overflows, input validation issues, or other security weaknesses.
Execution of Malicious Code:
The attacker creates or injects malicious code into the vulnerable program. When the SUID program is executed, it runs with elevated privileges, allowing the attacker to perform actions they wouldn't normally be allowed to do.
Gaining Elevated Privileges:
By exploiting the SUID program, the attacker may gain elevated privileges, enabling them to access sensitive files, manipulate system configurations, or perform other malicious activities.
Mitigation:
To prevent SUID exploitation, it's crucial to carefully review and audit programs with the SUID bit set. Remove unnecessary SUID permissions, and ensure that programs are secure and well-designed to resist exploitation.
Regular System Audits:
System administrators should conduct regular audits to identify and address potential security risks. This includes monitoring for changes in SUID permissions and reviewing the security of programs with elevated privileges.
Suid Exploits (PoC)
CP Command
Infact, if I try to use: find / -perm -u=s -type f 2>/dev/null there's not cp path (or in alternative see permissions of ls -al command_path_name). If we want to assign SUID permission at cp command, we need to use chmod u+s (path of cp command):
Now, every users can execute cp command with root permissions!
Then, we can execute the same sequence of commands regarding cp of /etc/passwd using new_user account user:
The idea is to add a new user with root permissions and not only for cp command.
Using openssl passwd we generate a password with MD5 algorithm (option -1) and custom salt
Then, construct our costum account string to append in /etc/passwd file based on this format:
<username>:<hash>:0:0:0:root:/root:/bin/bash
Add it in our local copy of /etc/passw using vim or nano or copy it in original file:
Finally we can log into new_root_user and have root privileges.
GTFOBins
In alternative we can do privilege escalation using commands present on GTFOBins site regarding cp command in the section of SUID:
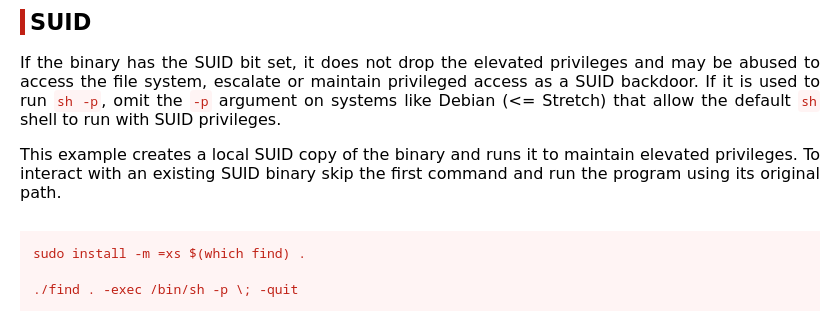
FIND Command
In the wake of the previous example, we proceed with the find command, using the same normal user (new_user).
To do privilege escalation we only need to file an existing file using find command:
GTFOBins
in alternative we can do privilege escalation using commands present on GTFOBins site regarding find command in the section of SUID:
NANO Command
As the last case, we do this sequence of command to do NANO SUID exploitation:
Now, we can open file with root permissions like as /etc/passwd with a normal user using nano:
As the example of Copy SUID, the idea is to add a new user with root permissions and not only for nano command.
Using openssl passwd we generate a password with MD5 algorithm (option -1) and custom salt
Then, construct our costum account string to append in /etc/passwd file based on this format:
<username>:<hash>:0:0:0:root:/root:/bin/bash
Add it in our local copy of /etc/passw using vim or nano or copy it in original file:
Finally we can log into new_root_user and have root privileges.
GTFOBins
in alternative we can do privilege escalation using commands present on GTFOBins site regarding nano command in the section of SUID:
RIGHT Command
Sudoers file can cantoins users with a specific root permission called SUDO Rights, e.g. new_user ca execute find command as root:
To do privilege escalation we only need to file an existing file using find command:
Can we do the same for others command, e.g. vi command:
It's possible to do the same for more command such as: man, python, nano, vim, etc.