📔eCPPT Cheat Sheet
Networking
Routing
# Linux
ip route
# Windows
route print
# Mac OS X / Linux
netstat -rIP
# Linux
ip a
ip -br -c a
# Windows
ipconfig /all
# Mac OS X / Linux
ifconfigARP
Ports
Connect and Scan
Information Gathering
Passive
Google Dorks
DNS
Host Discovery
Footprinting & Scanning
Network Discovery
Enumeration
SMB
Nmap
Nmblookup
SMBMap
SMB Connection
RPCClient
Enum4Linux
Hydra
We can use a wordlist generator tools (how Cewl), to create custom wordlists.
Metasploit
FTP
Nmap
Ftp Client
Hydra
SSH
Nmap
Netcat
SSH
Hydra
Metasploit
HTTP
Nmap
Alternative
Metasploit
SQL
Nmap
Hydra
Metasploit
SMTP
Nmap
Metasploit
Vulnerability Assessment
Host Based Attacks
Windows Exploitation
IIS WEBDAV
SMB
Nmap
Metasploit
RDP
WINRM
Windows Privilege Escalation
Kernel
UAC
Access Token
Windows Credential Dumping
Linux Exploitation
Shellshock
FTP
SSH
SAMBA
Linux Privilege Escalation
Kernel
Cron Jobs
SUID
Linux Credential Dumping
Network Based Attacks
Wireshark
TShark
Metasploit
Meterpreter
Info Gathering & Enumeration
Vulnerability Scanning
Payloads
MSFVenom shells
MSF Staged and Non Staged Payload
Win Exploitation
Default MSF Start
HFS
SMB
WINRM
TOMCAT
Linux Exploitation
FTP
SAMBA
SSH
SMTP
Post-Exploitation Fundamentals
Win Post-Exploitation
To search for files and Folders
HTTP/HFS
UAC
TOKEN IMPERSONATION
DUMP HASHES
PERSISTENCE
CLEARING
PIVOTING
Linux Post-Exploitation
Armitage
Exploitation
Vulnerability Scanning
Exploits
Shells
Frameworks
Win Exploitation
IIS/FTP
OPENSSH
SMB
MYSQL
Linux Exploitation
VSFTPD
Obfuscation
Post-Exploitation
Win Local Enumeration
Linux Local Enumeration
Transferring Files
Shells
TTY Shells
Win Privilege Escalation
Linux Privilege Escalation
Win Persistence
Linux Persistence
Dumping & Cracking
Windows
Linux
Pivoting
Clearing Tracks
Social Engineering
Web Application Penetration Testing
Tools
Enumeration & Scanning
Attacks
SQLMap
Check if injection exists
Get database if injection Exists
Get Tables in a Database
Get data in a Database tables
Get OS-Shell
XSS
Check an example:
Hijack cookie through xss
there are four components as follows:
attacker client pc
attacker logging server
vulnerable server
victim client pc
attacker: first finds a vulnerable server and its breach point.
attacker: enter the following snippet in order to hijack the cookie kepts by victim client pc (p.s.: the ip address, 192.168.99.102, belongs to attacker logging server in this example):
attacker: log into attacker logging server (P.S.: it is 192.168.99.102 in this example), and execute the following command:
attacker: when victim client pc browses the vulnerable server, check the output of the command above.
attacker: after obtaining the victim’s cookie, utilize a firefox’s add-on called Cookie Quick Manager to change to the victim’s cookie in an effort to hijack the victim’s privilege.
XSSer
Hydra
Wordpress
Basic Information
Uploaded files go to: http://10.10.10.10/wp-content/uploads/2018/08/a.txt
Themes files can be found in /wp-content/themes/, so if you change some php of the theme to get RCE you probably will use that path. For example: Using theme twentytwelve you can access the 404.php file in: /wp-content/themes/twentytwelve/404.php
Another useful url could be: /wp-content/themes/default/404.php
In wp-config.php you can find the root password of the database.
Default login paths to check: /wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/
Main WordPress Files
index.phplicense.txtcontains useful information such as the version WordPress installed.wp-activate.phpis used for the email activation process when setting up a new WordPress site.Login folders (may be renamed to hide it):
/wp-admin/login.php/wp-admin/wp-login.php/login.php/wp-login.php
xmlrpc.phpis a file that represents a feature of WordPress that enables data to be transmitted with HTTP acting as the transport mechanism and XML as the encoding mechanism. This type of communication has been replaced by the WordPress REST API.The
wp-contentfolder is the main directory where plugins and themes are stored.wp-content/uploads/Is the directory where any files uploaded to the platform are stored.wp-includes/This is the directory where core files are stored, such as certificates, fonts, JavaScript files, and widgets.
Post exploitation
The
wp-config.phpfile contains information required by WordPress to connect to the database such as the database name, database host, username and password, authentication keys and salts, and the database table prefix. This configuration file can also be used to activate DEBUG mode, which can useful in troubleshooting.
Users Permissions
Administrator
Editor: Publish and manages his and others posts
Author: Publish and manage his own posts
Contributor: Write and manage his posts but cannot publish them
Subscriber: Browser posts and edit their profile
Passive Enumeration
Get WordPress version
Check if you can find the files /license.txt or /readme.html
Inside the source code of the page (example from https://wordpress.org/support/article/pages/):
Grep
Meta name
CSS link files
JavaScript files
Get Plugins
Get Themes
Extract versions in general
Active enumeration
Plugins and Themes
You probably won't be able to find all the Plugins and Themes passible. In order to discover all of them, you will need to actively Brute Force a list of Plugins and Themes (hopefully for us there are automated tools that contains this lists).
Users
ID Brute
You get valid users from a WordPress site by Brute Forcing users IDs:
If the responses are 200 or 30X, that means that the id is valid. If the the response is 400, then the id is invalid.
wp-json
You can also try to get information about the users by querying:
Only information about the users that has this feature enable will be provided.
Also note that /wp-json/wp/v2/pages could leak IP addresses.
Login username enumeration
When login in /wp-login.php the message is different is the indicated username exists or not.
WPScan
Drupal
Discovery
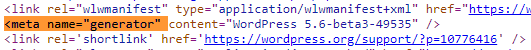
Check meta
Node: Drupal indexes its content using nodes. A node can hold anything such as a blog post, poll, article, etc. The page URIs are usually of the form
/node/<nodeid>.
Enumeration
Drupal supports three types of users by default:
Administrator: This user has complete control over the Drupal website.Authenticated User: These users can log in to the website and perform operations such as adding and editing articles based on their permissions.Anonymous: All website visitors are designated as anonymous. By default, these users are only allowed to read posts.
Version
Check
/CHANGELOG.txt
{% hint style="info" %} Newer installs of Drupal by default block access to the CHANGELOG.txt and README.txt files. {% endhint %}
Username enumeration
Register
In /user/register just try to create a username and if the name is already taken it will be notified:
Request new password
If you request a new password for an existing username:
If you request a new password for a non-existent username:
Get number of users
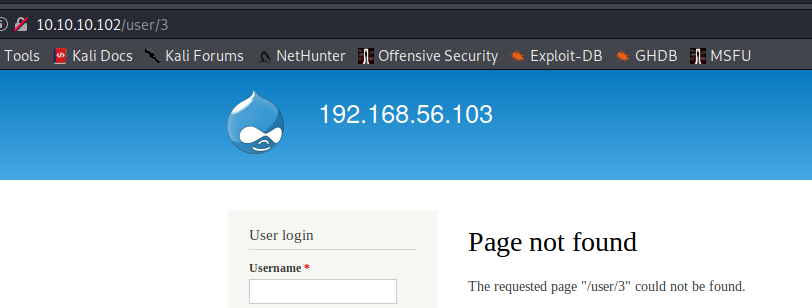
Accessing /user/<number> you can see the number of existing users, in this case is 2 as /users/3 returns a not found error:
Hidden pages
Fuzz /node/$ where $ is a number (from 1 to 500 for example).
You could find hidden pages (test, dev) which are not referenced by the search engines.
Installed modules info
Automatic
RCE
With PHP Filter Module
{% hint style="warning" %} In older versions of Drupal (before version 8), it was possible to log in as an admin and enable the PHP filter module, which "Allows embedded PHP code/snippets to be evaluated." {% endhint %}
You need the plugin php to be installed (check it accessing to /modules/php and if it returns a 403 then, exists, if not found, then the plugin php isn't installed)
Go to Modules -> (Check) PHP Filter -> Save configuration
Then click on Add content -> Select Basic Page or Article -> Write php shellcode on the body -> Select PHP code in Text format -> Select Preview
Finally just access the newly created node:
Install PHP Filter Module
From version 8 onwards, the PHP Filter module is not installed by default. To leverage this functionality, we would have to install the module ourselves.
Download the most recent version of the module from the Drupal website.
Once downloaded go to
Administration>Reports>Available updates.Click on
Browse,select the file from the directory we downloaded it to, and then clickInstall.Once the module is installed, we can click on
Contentand create a new basic page, similar to how we did in the Drupal 7 example. Again, be sure to selectPHP codefrom theText formatdropdown.
Backdoored Module
A backdoored module can be created by adding a shell to an existing module. Modules can be found on the drupal.org website. Let's pick a module such as CAPTCHA. Scroll down and copy the link for the tar.gz archive.
Download the archive and extract its contents.
Create a PHP web shell with the contents:
Next, we need to create a
.htaccessfile to give ourselves access to the folder. This is necessary as Drupal denies direct access to the/modulesfolder.
The configuration above will apply rules for the / folder when we request a file in /modules. Copy both of these files to the captcha folder and create an archive.
Assuming we have administrative access to the website, click on
Manageand thenExtendon the sidebar. Next, click on the+ Install new modulebutton, and we will be taken to the install page, such ashttp://drupal-site.local/admin/modules/installBrowse to the backdoored Captcha archive and clickInstall.Once the installation succeeds, browse to
/modules/captcha/shell.phpto execute commands.
Post Exploitation
Read settings.php
Dump users from DB
[CVE-2018-7600] Drupalgeddon 2
https://ine.com/blog/cve-2018-7600-drupalgeddon-2
In late March 2018, a critical vulnerability was uncovered in Drupal CMS. Drupal before 7.58, 8.x before 8.3.9, 8.4.x before 8.4.6, and 8.5.x before 8.5.1 versions were affected by this vulnerability.
It allows remote attackers to execute arbitrary code because of an issue affecting multiple subsystems with default or standard module configurations.
A lot of PoC is available to exploit this vulnerability.
References (tranks to all):
https://blog.syselement.com/ine/courses/ejpt
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/