Active

Task 1 - Deploy the machine
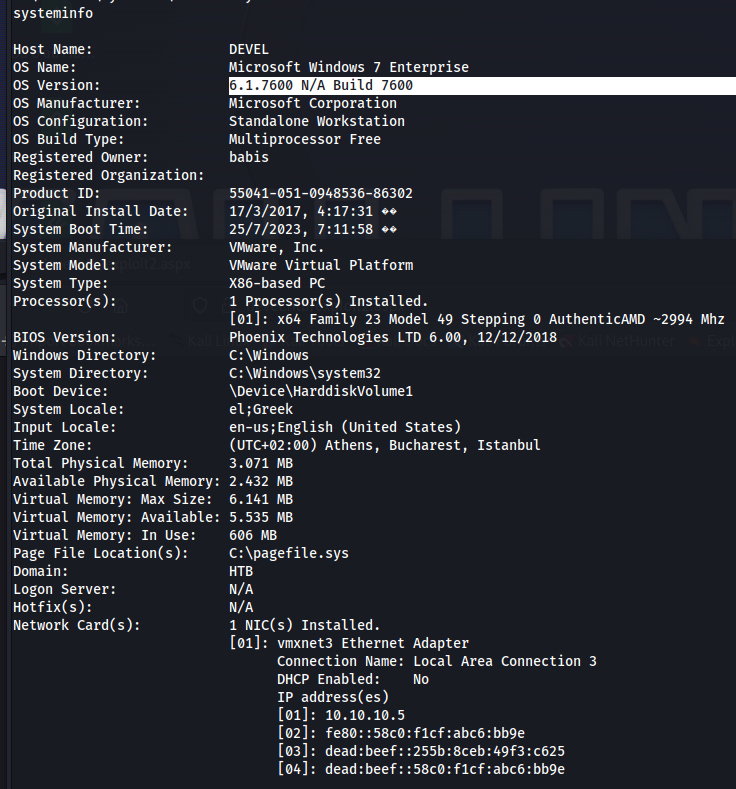
Task 2 - Reconnaissance
2.1 - What is the name of the service is running on TCP port 21 on the target machine?
21 on the target machine?command
result
2.2 - Which basic FTP command can be used to upload a single file onto the server?
2.3 - Are files put into the FTP root available via the webserver?
2.4 - What file extension is executed as a script on this webserver? Don't include the ..
..2.5 - Which metasploit reconnaissance module can be used to list possible privilege escalation paths on a compromised system?

Task 3 - Find user flag
3.1 - Submit the flag located on the babis user's desktop.