Command Injection
http://localhost/DVWA/vulnerabilities/exec/
What is a command injection?
Command injection is a type of security vulnerability that occurs when an attacker is able to inject and execute arbitrary commands or code into a software application. This vulnerability is typically found in applications that accept and process input from users or other untrusted sources without proper validation or sanitization.
The most common form of command injection involves the exploitation of input fields or parameters that are used to construct system commands. When the application fails to properly validate or sanitize user input, an attacker can inject malicious commands that get executed by the underlying system with the privileges of the application.
Using BurpSuite and the FoxyProxy extension is recommended.
Low
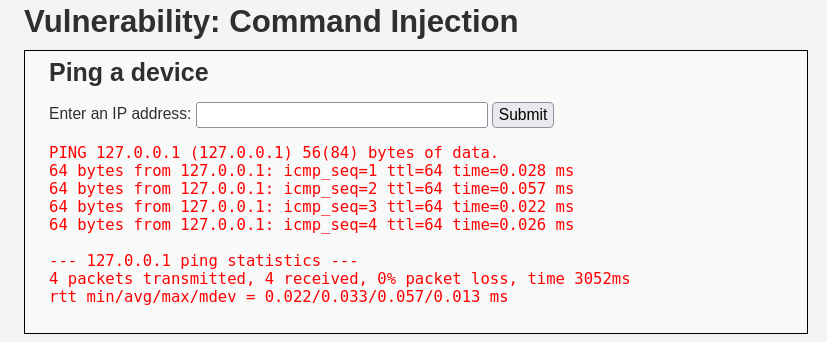
We've a form with an input type text:

that ask us to enter and IP address to ping.
Inserting an IP address we can confirm that will do a ping request to it:
As always we can start to analyze source code:

There'is a condition to check if input value has been inserted
The operating system in use is checked to evaluate exactly which ping should be entered (win or *nix OS)
In the end, there's generate feedback for the end user.
The input is not sanitized, so I can execute any (potentially malicious) command.
Payload
using it, we ping machine with IP 127.0.0.1 and join two extra commands using ; or another join char as |, to take a whoami and see /etc/passwd file:

Medium

There's a classic control of input text submitted
An eventually blacklist word (&& and ;) is replace with a '' black char
The operating system in use is checked to evaluate exactly which ping should be entered (win or *nix OS)
In the end, there's generate feedback for the end user.
The input is not sanitized because blacklist words are eventually removed only one time and not recursevely and we can use others join chars to add a new commands such as |.
Payload
We've replaced ; or && with |:

; will be replace by '' and will submit this prohibit payload:

High
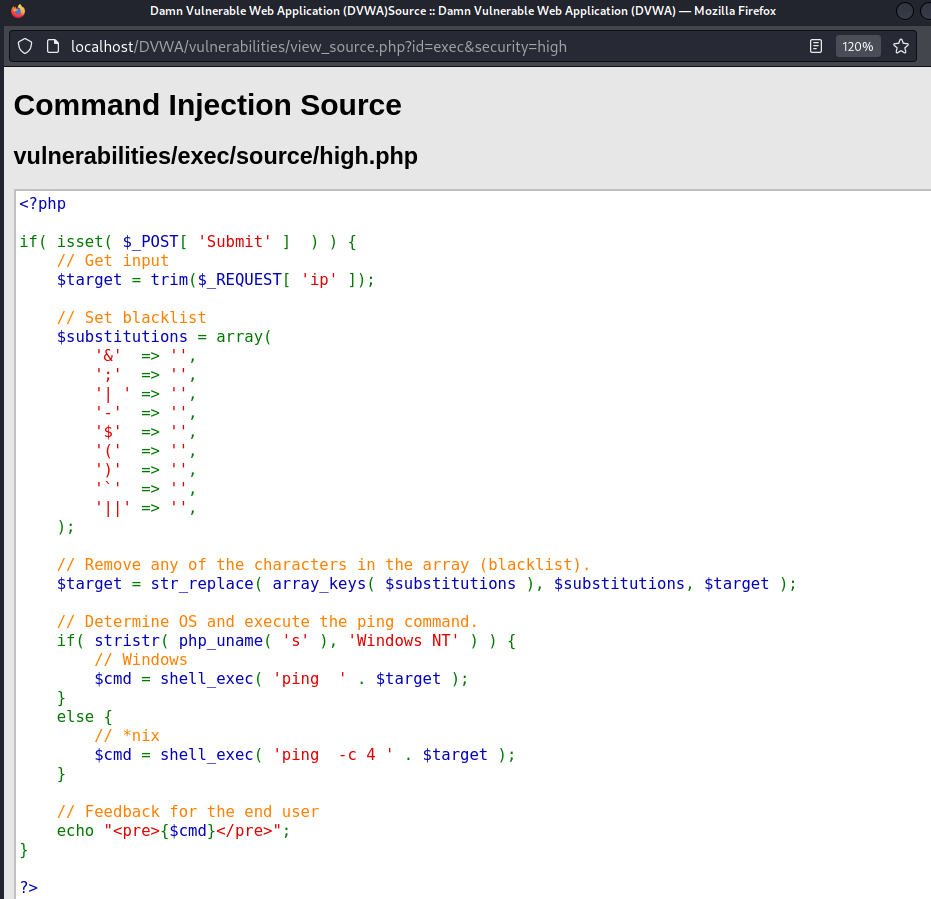
This command isn't write correctly, it has an extra space '| '

The input is not sanitized, so I can execute any (potentially malicious) command.
Payload
Without leaving a white space after | we can use this payload:

Impossible

The input is sanitized and it's not vulnerable to a command injection attack.
References
For the making of this solution the following resource were used: